Trojan.PWS.OSMP.21 infects payment terminals
Real-time threat news | Hot news | All the news | Virus alerts
March 25, 2014
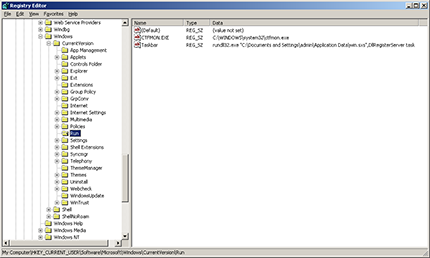
Trojan.PWS.OSMP.21 is implemented as a dynamic link library which is delivered onto terminals via infected flash drives. A dropper program responsible for copying the dll file has also been discovered. Once the payment terminal has been compromised, the Trojan library is copied into the Application Data folder as win.sxs. Then one of its routines is used to modify the Windows Registry for the dll file to auto load at system start-up. The added registry entry name is Taskbar.
Next, another malignant routine searches for the process involved in payment processing. If it does not find this process, it initiates another routine that infects flash drives. If the targeted process is active, Trojan.PWS.OSMP.21 tries to retrieve the config.dat file and the logs from the folder containing the corresponding executable file, and gathers information about the hard disk. Subsequently, all the data is transmitted in an encrypted format to the attacker's server. If the data transfer is successful, the Trojan will delete itself.
Trojan.PWS.OSMP.21’s signature was added to the Dr.Web virus database on February 14. Doctor Web's anti-virus programs successfully detect and remove this malware.