Android adware “sets up” other programs
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
November 27, 2015
Android.Spy.510 is distributed by cybercriminals as a modified and initially non-threat AnonyPlayer media application. Its Trojan version has all the legitimate functions and is absolutely operational—thus, the victim will not be suspicious about the threat it can potentially pose.
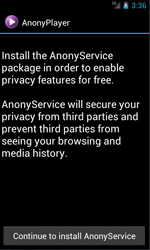
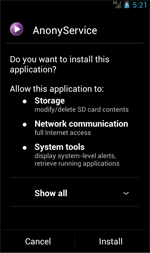
Once installed and launched, Android.Spy.510 gathers and sends confidential data to the command and control server (C&C server) including the following information: login and password to the Google Play user account, mobile device model, SDK version of the operation system, and availability of root access on the device. Then the Trojan tries to install an additional hidden program package with necessary malicious features. To do that, Android.Spy.510 displays a special text message which offers the victim to install the AnonyService application that is supposed to assure users` anonymity and to protect confidential information from third parties. However, this application is, in fact, an advertising module added to Dr.Web virus database under the name of Adware.AnonyPlayer.1.origin.
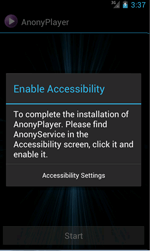
After the installation, Adware.AnonyPlayer.1.origin immediately prompts the victim to allow the use of the Accessibility Service. Then it goes to a standby mode and starts its malicious activity only in several days. Therefore, the possibility of detecting the source of infection on a compromised device by the user is really low.
Once the specific period of time is over, Adware.AnonyPlayer.1.origin starts to monitor all system events and waits for the victim to run some program. If they do so, the module immediately displays an advertisement. First, Adware.AnonyPlayer.1.origin checks if the corresponding program is on the white list that contains the applications without advertising features:
- org.adw.launcher
- com.android.launcher
- com.android.systemui
- com.android.settings
- com.android.dialer
- com.huawei.android.launcher
- com.google.android.gm
- com.android.deskclock
- com.android.calendar
- com.android.contacts
- com.sec.android.app.camera
- com.lge.settings.easy
- com.android.providers.downloads.ui
- com.android.calculator2
- com.android.mms
- com.android.phone
- android
- com.lge.clock
- com.sec.android.app.launcher
- com.android.gallery
- com.android.camera
- com.google.android.apps.maps
- com.lge.launcher2
- com.apusapps.launcher
- com.lge.splitwindow
- com.sonyericsson.home
- com.android.incallui
- com.google.android.inputmethod.latin
- com.whatsapp
- com.android.packageinstaller
If the program is on the list, Adware.AnonyPlayer.1.origin does not run since advertisements shown after the launch of a “clean” program can alert the user and lead to detection of their real source.
If there is no correspondence found, Adware.AnonyPlayer.1.origin creates a special message using WebView which is displayed on top of the launched program and contains the advertisement specified by the C&C server. As a result, the owner of a compromised device may think that it is the launched application that is responsible for annoying notifications. What is more, in order to divert any suspicion from the malicious media player, Adware.AnonyPlayer.1.origin, as well as Android.Spy.510, is launched without advertising content.
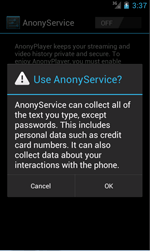
Doctor Web security researchers strongly recommend Android devices owners to download applications only from reliable sources. Besides, users should pay careful attention to the programs that request to allow them the use of the Accessibility Service. Once the malicious application gets such privileges, it can interact with graphic interface (for example, simulate user actions in dialogs) and even intercept the information entered by the victim, operating as a keylogger. As a result, the program will be able to steal such confidential data as text messages, search queries and even passwords.
The signatures of Android.Spy.510 and Adware.AnonyPlayer.1.origin have been added to Dr.Web virus database. Therefore, these malicious programs pose no threat to our users.