Dr.Web Security Space for Android can now remove rootkits
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
November 19, 2015
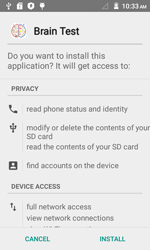
One of the integrated protection mechanisms in Android OS is implemented through the installation routine—that is, installation proceeds only after the user gets familiar with information on this or that program (including the features that program will be able to access) and gives their consent to continue. That is why it is not surprising that virus makers try to bypass this limitation by equipping their Trojans with various root exploits that give them unlimited privileges to perform various malicious activities on attacked mobile devices. As a result, already in 2011 there appeared Android malware that could get system privileges by exploiting different program vulnerabilities and then install and remove software without user consent. In particular, such Trojans as Android.DreamExploid and Android.Gongfu distributed in programs modified by virus makers belong to this category.
Nevertheless, cybercriminals were not that eager to employ such programs for their attacks preferring to use “less advanced” software. However, in 2015, Doctor Web security researchers registered a new wave of increased interest in rootkits. At that, if previously cybercriminals used such program to install as many affiliate programs as they could to get a reward for every successful installation, now they try to embed malware directly into an Android system folder. In other words, cybercriminals want to infect mobile devices with rootkits that stay hidden in the system and continue to operate even if the malicious program that installed them is removed from the device.
Once such Trojans get into the system area, they acquire elevated privileges providing cybercriminals with full control over infected devices and information stored on them. At that, detection of such applications that are not known to security researchers becomes rather hard and may take more time compared to identification of “ordinary” malware for Android.
However, even after Android rootkits are successfully detected in a system folder, their removal is associated with a number of risks—for example, in numerous cases such programs significantly modify software environment (in particular, they can replace some original applications required for normal operation of the device with malicious ones), and, as a result, if the user tries to remove them, the operation can render the device “dead”. Nonetheless, even in such cases it is rather easy to restore it back to life—for that, one just needs to reinstall the original firmware. However, some anti-virus vendors claim that it is almost impossible to remove Trojans from the system area, and users who got into such trouble should seriously consider buying a new mobile device.
In reality, Android rootkits can be successfully dealt with. Doctor Web specialists thoroughly examine every malicious application of such type and carefully analyze all instances of the malware being detected in a system folder. Once security researchers make sure that removal of a Trojan does not render an Android device unresponsive, a corresponding curing algorithm is recorded to the virus database of Dr.Web Security Space for Android. Despite the fact that this process is very time and recourse consuming, the total number of Trojans successfully removed from the system area is growing every day. Since the program bearing all the necessary features was updated on October 19, our users are already effectively fighting against hundreds of various modifications of Android rootkits hiding in a system folder for one whole month. For the anti-virus to be able to remove such Trojans, the user just needs to grant it root privileges.
In 2015, security researchers detected a large number of malicious applications that tried to get root privileges and stealthily install other malware into system folders. Among them were the Trojans belonging to the Android.Toorch family—they came into spotlight in April of the current year. One of them was disguised as a torch application and was distributed via popular Chinese websites with downloadable software. Furthermore, the malware could be downloaded to mobile devices with the help of numerous aggressive advertising modules embedded into different applications. Once launched, the Trojan tried to acquire root privileges, install into the /system/app folder one of its components, and run another malicious module. Upon a command from cybercriminals, the malware could download, install, and remove specified programs without user knowledge.
Another malicious program that tried to get root privileges was dubbed by Doctor Web Android.Backdoor.176.origin and was distributed via games and applications modified by cybercriminals. Once launched, Android.Backdoor.176.origin forwards the command and control server detailed information regarding the infected device. After that, it registers several system event listeners controlling, in particular, OS loading, any user interactions with the screen, running of applications, and so on. After the infected device is turned on, the malicious program downloads from the Internet a modified version of Root Master and, using it, tries to get root privileges. If successful, the Trojan copies two executable ELF files—the .rt_bridge file (Android.Rootkit.1) and the .rt_daemon file (Android.Rootkit.2)—to the /system/xbin folder. These two files have the same features as the SU utility that allows users to work with root (administrator) privileges on UNIX-like systems.
Once launched, Android.Rootkit.1 checks whether it is run by one of the processes belonging to Android.Backdoor.176.origin and, if so, starts a root terminal. Then Android.Backdoor.176.origin downloads the chattr utility from the Internet and, using this utility, sets the “immutable” and “append only” attributes for its own APK file via the terminal. As a result, even if the user uninstalls the Trojan, once the system is rebooted, Android.Backdoor.176.origin will be reinstalled, and the mobile device will stay infected.
The main purpose of this program is to stealthily install and remove applications upon a command from the command and control server. In addition to that, the Trojan forwards detailed information regarding the infected device to cybercriminals and monitors incoming and outgoing calls and messages.
Some time later, security researchers detected a new modification of this malicious program and dubbed it Android.Backdoor.196.origin. Similar to the first version, it is distributed via games and applications modified by cybercriminals. Once launched, it also tries to acquire root privileges and protect itself against being removed. After that, Android.Backdoor.196.origin launches its second component using DexClassLoader. Depending on the modification of the Trojan, the second component is either downloaded from a remote server or extracted from the Trojan’s body and then decrypted. Subsequently, this module, detected by Dr.Web for Android as Adware.Xinyin.1.origin, performs all malicious activities. In particular, it can download and install various programs, send text messages, monitor incoming and outgoing calls and messages.
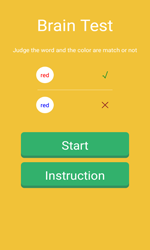
Later, security researchers detected a few other malicious programs that tried to get root privileges and posed a serious threat to users of mobile devices. Android.Backdoor.273.origin was one of them. The backdoor was incorporated into the application called Brain Test and had a number of interesting features. In particular, once launched, the Trojan checked the IP address of the domain used for establishing network connection on the device. If it corresponded to a Google address, the malware terminated its work. This technique allowed cybercriminals to get past the Google Bouncer. Once the malicious program made sure that it was safe to run, it established a connection to the command and control server and downloaded four exploits in order to get root privileges. If successful, the Trojan downloaded another malicious component which was installed into a system folder. Upon a command from cybercriminals, that module could stealthily download and install other malware on the compromised device. Moreover, to stay on the device as long as possible, Android.Backdoor.273.origin installed into a system folder two additional malicious components that constantly checked integrity of each other and, if one of them (or Android.Backdoor.273.origin) was removed, downloaded necessary files and infected the device once again.
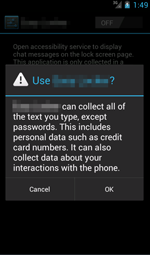
Another Trojan, which was dubbed Android.DownLoader.244.origin, also poses a significant threat to users of Android smartphones and tablets. Like many other malicious applications for Android, it was distributed through websites that host various software for mobile devices and was incorporated into originally harmless games and applications. Once a program containing Android.DownLoader.244.origin was launched, the Trojan prompted the user to enable the malicious Accessibility Service. If the victim followed the instructions and enabled the corresponding Accessibility Service, the malicious program became able to monitor all system events and install various applications specified by cybercriminals on behalf of the user and without their consent. After that, the Trojan tried to get root privileges in order to download and install different programs into a system folder upon a command from the command and control server.
However, Android Trojans that get root privileges to freely perform their malicious activities on compromised devices are not the only threat that users have to face. Malicious programs that do not ask for root privileges but still abuse them if they are available are no less dangerous. For example, such Trojan as Android.DownLoader.171.origin that was disguised as KKBrowser and was distributed through Google Play and other Internet resources, which resulted in the total number of downloads exceeding 1.5 million. Upon a command from its creators, the malware could install and remove various programs. If root access was available, Android.DownLoader.171.origin performed those actions automatically (otherwise, the user was asked to give their consent).
To protect your Android device from Trojans that try to get root access and install malicious applications into system folders, it is strongly recommended that you download applications only from trusted sources. Also, it is advised that you never install any applications that look suspicions. Moreover, to effectively withstand malicious, unwanted, and potentially dangerous applications for Android devices, it is very important that a reliable anti-virus software, which can not only detect a threat but also remove it, should be installed on your device.