Dangerous encryption ransomware spreading via email
Real-time threat news | Hot news | All the news | Virus alerts
March 20, 2015
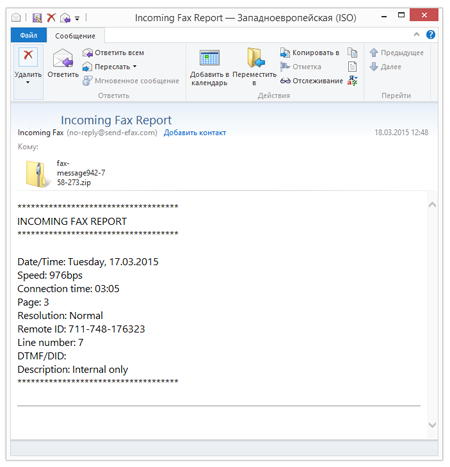
Over the past few months, attackers have organized many spam campaigns to spread different encryption ransomware versions. For example, last week witnessed a growing number of incidents involving mass mailings of new incoming fax messages with the headline "Incoming Fax Report". Disguised as a fax message, the attached ZIP archive contains a malicious SCR file—a Windows executable. These SCR files are detected by Dr.Web anti-virus software as Trojan.DownLoader11.32458.
If an attempt is made to open the attachment, the malicious program Trojan.DownLoader11.32458 extracts and launches the encryption ransomware Trojan.Encoder.514 on the target machine. The ransomware then encrypts data stored on the disk and demands a ransom for its recovery. Files affected by Trojan.Encoder.514 do not have their filename extension changed, but get the string "!crypted!" appended at the beginning of their names. During the encryption process, the malware creates temporary files with the extension *.cry which are later deleted.
It is currently impossible to decrypt files affected by Trojan.Encoder.514. Doctor Web encourages users to make timely backups of their most valuable data, and to stay vigilant and refrain from opening files attached to emails from unknown senders.
Use Data Loss Prevention to protect your files from encryption ransomware
| Only available in Dr.Web Security Space 9 and 10 |
| More about encryption ransomware |  |
Configuration presentations tutorial |  |
Free decryption |