New Trojan for Android exploits vulnerability to hide from anti-viruses
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
October 16, 2013
The new Trojan, dubbed by Dr.Web as Android.Spy.40.origin, is spread by means of unwanted SMS messages containing a link to an apk file. Among cybercriminals in Southeast Asia (mainly South Korea and Japan), it is currently one of the most popular techniques for spreading Android malware. Once Android.Spy.40.origin is installed and launched, it requests access to OS administrative features, removes its icon from the main screen, and covertly maintains its operation in the system.
Then the Trojan connects to a remote server from which it receives further instructions. In particular, Android.Spy.40.origin can perform the following tasks:
- Intercept inbound short messages and upload them to the server (messages are hidden from the user).
- Block outgoing calls.
- Send a list of contacts or installed applications to the server.
- Remove or install the application specified in the received command.
- Send a message with a defined text to a specified number.
This malicious program can pose a severe threat because it intercepts messages that may contain confidential information, personal and business correspondence, bank account information and mTAN-codes used to verify transactions. In addition, the contacts list acquired by cybercriminals can then be used to send bulks of SMS spam and mount phishing attacks.
However, Android.Spy.40.origin’s principal distinguishing feature is its ability to exploit an Android vulnerability to avoid detection by anti-viruses. To conceal the malware, attackers modified the Trojan's apk file (an apk file is a standard zip archive with a different extension).
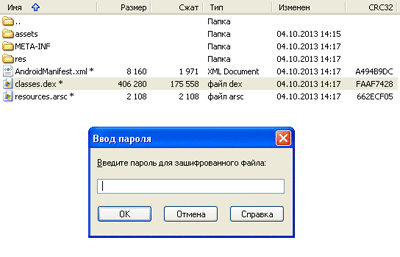
According to the zip file’s format specification, the archive header for each compressed file within it includes the field ‘General purpose bit flag’. A zero bit fixed in this field indicates that the files in the archive are encrypted (password protected). In other words, despite the absence of a password, when a bit is set to 1, the file must be treated as encrypted.
As you can see in the picture above, under normal circumstances, a password prompt is displayed when one tries to unpack such zip files, but due to a flaw in Android, the zero bit is ignored, which allows a program to be installed. In contrast with an operating system that has this vulnerability, various anti-virus programs are obligated to correctly handle the field ‘General purpose bit flag’, and as such, assume that the file is password-protected and thus not in need of scanning even if the definition for the malicious file contained in the apk package is in the virus database.
Doctor Web's engineers promptly made adjustments to its Dr.Web for Android anti-virus so that it successfully detects malware that makes use of the exploit described above. However, Android users are strongly recommended to exercise caution and refrain from installing suspicious applications and clicking on links in unwanted SMS messages.