Trojan.Rbrute hacks Wi-Fi routers
Real-time threat news | Hot news | All the news | Virus alerts
March 5, 2014
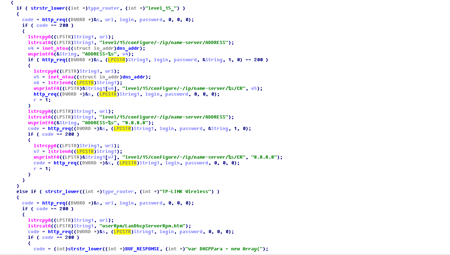
When launched on a Windows computer, Trojan.Rbrute establishes a connection with the remote server and stands by for instructions. One of them provides the Trojan with a range of IP addresses to scan. The Trojan can crack passwords for the following router models: D-Link DSL-2520U, DSL-2600U, TP-Link TD-W8901G, TD-W8901G 3.0, TD-W8901GB, TD-W8951ND, TD-W8961ND, TD-8840T, TD-8840T 2.0, TD-W8961ND, TD-8816, TD-8817 2.0, TD-8817, TD-W8151N, TD-W8101G, ZTE ZXV10 W300, ZXDSL 831CII. In fact, the Trojan is able to execute two commands:
- Scan the network using the specified range of IP addresses.
- Mount a dictionary attack.
These commands are unrelated and can be performed by the Trojan separately. If the network scan reveals an operational router, Trojan.Rbrute will retrieve a web page from the device, use the tag 'realm=\"' to determine its model and send a corresponding report to the remote server.
The Trojan can also be instructed to carry out a dictionary attack on the router. The instructions will contain all the necessary input data including the IP address of the target, the DNS server address to be replaced and the password dictionary. Trojan.Rbrute uses 'admin' or 'support' as a login.
If authentication involving a selected combination of the login and password is successful, the Trojan reports back to the remote server that the hacking was successful and instructs the router to change the DNS addresses stored in its settings. As a result, when a user tries to visit a website, they can be redirected to another site that has been crafted by intruders. This scheme is currently being used by cybercriminals to expand the botnet created using the malware Win32.Sector.
The general scheme used by intruders is as follows:
- In a compromised system, Win32.Sector downloads Trojan.Rbrute.
- Trojan.Rbrute receives a command to search for Wi-Fi routers and the password dictionary from a command and control server.
- If successful, Trojan.Rbrute modifies the router's DNS server settings.
- When another 'healthy' machine attempts to connect to the Internet through the compromised router, the user is redirected to a specially crafted web page.
- From this page, Win32.Sector malware is downloaded onto the computer and infects it.
- Subsequently Win32.Sector can download a copy of Trojan.Rbrute on the infected PC. The cycle repeats itself.
Trojan.Rbrute signature has been added to the Dr.Web virus database. Doctor Web recommends that Wi-Fi router owners change their default settings and use strong passwords that will be hard to crack with brute force attacks.