April 3, 2014
The greatest number of malicious and potentially unwanted programs—334,212—was detected by Dr.Web for Android on March 13, 2014. On the opposite end of the spectrum, March 11 accounts for the fewest number of malware incidents—244,478. The daily average was roughly 250,000 threats.
Most often, Dr.Web for Android detected various kinds of adware designed to help generate profits from free Android apps: Adware.Revmob, Adware.Airpush and Adware.Leadbolt, among other programs. Android.SmsBot.42.origin, intended mainly for the covert distribution of SMS messages to premium numbers, was the most frequently detected program. An application with similar functionality — Android.SmsSend.1088.origin — ranked second. The ten most common threats discovered on mobile devices by Dr.Web in March are presented in the table below.
| № | Threat name | % |
|---|---|---|
| 1 | Android.SmsBot.42.origin | 3,24 |
| 2 | Android.SmsSend.1088.origin, Android.SmsSend.458 | 1,80 |
| 3 | Android.SmsSend.315.origin | 1,75 |
| 4 | Android.SmsSend.1123.origin | 1,66 |
| 5 | Android.SmsSend.859.origin | 1,52 |
| 6 | Android.Spy.83.origin | 1,39 |
| 7 | Android.SmsBot.45.origin | 1,33 |
| 8 | Android.SmsSend.466.origin | 1,23 |
| 9 | Android.SmsSend.939.origin | 0,94 |
| 10 | Android.SmsSend.758.origin | 0,91 |
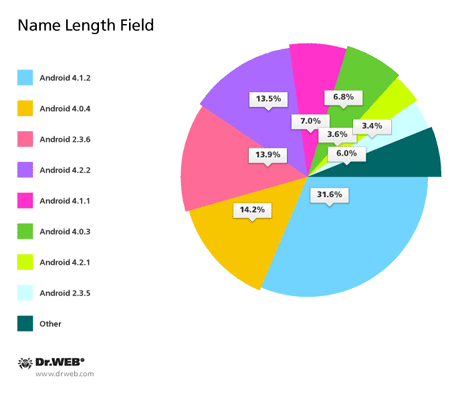
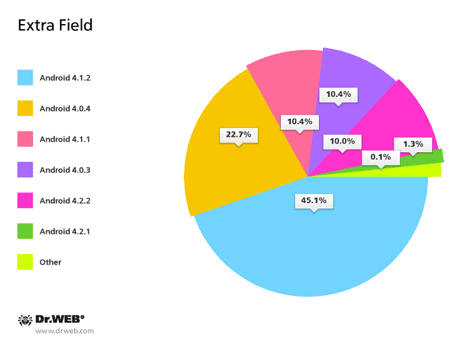
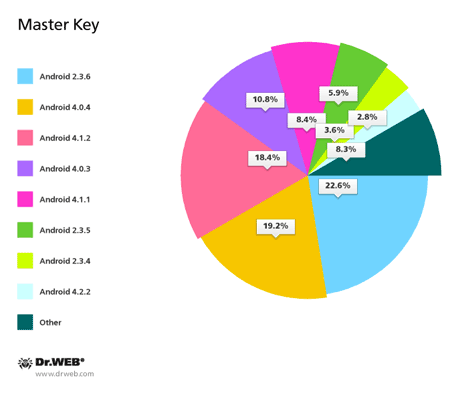
Dr.Web Anti-virus for Android includes a special component—the Security Auditor. It is designed to search for various operating system vulnerabilities that can be exploited by hackers or malicious software to carry out attacks on Android-powered devices. The Dr.Web anti-virus can identify several such loopholes. One of them—Master Key—is the flaw in Android security routines that makes it possible to install unsigned applications from packages containing files with identical names. Two other vulnerabilities—Extra Field and Name Length Field—can theoretically allow attackers to include in a tampered apk package a Trojan executable that will successfully pass automatic verification during installation. Thus, the potential danger exists for a malignant application to penetrate a device without the OS detecting it as a threat.
As of March 31, 2014, Dr.Web identified the vulnerability Name Length Field on 80.19% of protected devices, and the vulnerabilities Extra Field and Master Key were found on 48.56% and 46.95% of devices, respectively (sometimes several vulnerabilities are found on a single device). The pie charts below provide information about Android versions affected by the vulnerabilities.
Thus, today, vulnerabilities are most frequently identified in Android 4.1.2 and 4.0.4, with version 4.1.2 being one of the most common (it is installed on devices belonging to 27.16% of Dr.Web users). Version 4.0.4 only ranks third in popularity (21.14% of devices). It is surpassed by Android 2.3.3-2.3.7. According to statistics collected by Doctor Web, most Android firmware containing vulnerabilities is found on mobile devices from a renowned Korean manufacturer. Mobile phones and tablets from obscure Chinese companies rank second; in third and fourth place, respectively, are devices from a popular Taiwanese firm and another well-known South Korean company.
Devices can also get infected if their users fail to comply with security rules. According to our statistics, 49.74% of users adjusted operating system settings to enable the option to install applications from unknown sources. 14.8% of users enabled the USB debug mode, which could potentially result in a total data breach.
3.89% of users use rooted devices with administrator privileges, which also opens up unlimited opportunities for malicious programs when they reach the smart phone or tablet. And 13.3% of devices use third-party Android firmware, the kind that is typically distributed by numerous Chinese manufacturers. Such firmware also provides malware with extra opportunities, and users often do not even know about the risks.
Doctor Web will continue to closely monitor the spread of malware for Android and inform users about the potential dangers.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live




![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments