Twenty eight apps on Google Play spread Trojans
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
April 23, 2013
Advertising in applications for Android has long been successfully used by various developers to generate income from their work: it is a legal and a very convenient way to get compensated for time and money spent creating software. It was in 2011 when crafty cybercriminals also decided to use mobile ad networks to spread Trojans. Android.SmsSend programs designed to send short messages to premium numbers and subscribe users to chargeable services are the most popular among them. Doctor Web recently reported an incident involving such a program. However, the list of malware being spread in such a way is expanding.
Despite the fact that ad networks like Google AdMob, Airpush, and Startapp meet criminals' demands, intruders decided to go even further and created an ad network of their own. At first sight, it appears quite similar to others: Android software developers are offered very favourable advertising API usage terms, and are promised a high and steady income and easy account management. So it's hardly surprising that some developers became very interested in the ad network.
The advertisement API provides push notification ads that deliver small alerts to an Android phone's notification bar. However, there are also some undocumented features.
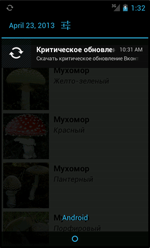
Push ads sent via the ad network can prompt a user to install an important update for a certain application. If an unsuspecting user agrees to install this update, the advertising module downloads an apk package and places it into the download directory /mnt/sdcard/download on the memory card. The module can also create a shortcut linked to the downloaded package, so if the user taps on it, it will start the installation of the downloaded program.
An investigation conducted by Doctor Web's analysts revealed that such apk-files contain Android.SmsSend Trojans. Analysts also found that these malicious programs were being downloaded from various fake application catalogues. The ad module in three analysed applications would connect to a control server at 188.139.xxx.xx, while the module in the remaining 25 apps would try to connect to a server at 91.226.xxx.xx. These IP addresses were promptly added to the Dr.Web Parental Control database, so access to the respective sites is blocked.
Below you can find a full list of the commands sent by a controlling server to the malignant module:
- news – display a push-notification
- showpage – open a web page in a browser
- install – download and install an apk package
- showinstall – show a push-notification about the installation of an apk package
- iconpage – create a shortcut to a web page
- iconinstall – create a shortcut to the downloaded apk package
- newdomen – change the control server address
- seconddomen – an alternate server address
- stop – stop sending queries to the server
- testpost – re-send a request
- ok – do nothing
In addition to executing these commands, the fraudulent module is also able to collect and send the device's IMEI, operator code, and the phone number to the server.
The advertising API is particularly dangerous because applications that use it are found on Google Play, which de facto is the safest sourceof programs for Android. Many users have come to trust the security of Google Play, so the number of installations of the software that feature the advertising module is very large. Since statistics about downloads of applications from Google Play are hard to get, Doctor Web can't say exactly how many devices have been compromised, but it can be assumed that the number exceeds 5.3 million handhelds. This is the largest and most massive case of infection on Google Play since Google Bouncer was introduced.
Considering the advertising API’s malignant features and the connection between the ad network and sites spreading malware for Android, Doctor Web has classified this module as belonging to adware designed to perform malicious tasks. The module has been added to the virus databases as Android.Androways.1.origin and poses no threat to devices running Dr.Web anti-virus for Android.