Linux.Sshdkit attacks Linux servers
Real-time threat news | All the news | Virus alerts
February 22, 2013
The malware is a library file available for 32- and 64-bit versions of Linux distributions. How the Trojan spreads is yet to be determined, but there are reasons to believe that it exploits critical vulnerabilities to become installed on attacked servers. The latest Trojan version known to Doctor Web is 1.2.1, while one of the earliest—1.0.3—has been spreading for quite a while.
After successful installation, the Trojan injects its code into the process sshd and uses this process’s authorization routines. Once a session is started and a user enters their login and password, the Trojan sends them to a remote server via UDP. The control server’s IP is hardcoded into the malware. However, every two days, the Trojan generates a new command server address by employing a non-trivial routine.
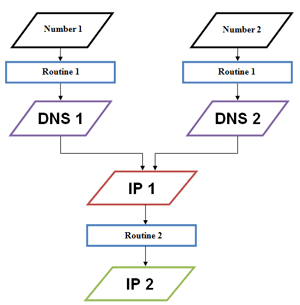
Linux.Sshdkit uses a special algorithm to generate two DNS names, and if they both refer to the same IP address, that address is converted to a different IP to which the Trojan sends the stolen information. The routine used to generate command server addresses is outlined in the flowchart below.
Doctor Web's analysts used a sinkhole to hijack one of Linux.Sshdkit control servers and thus confirmed that the Trojan sends stolen logins and passwords to remote hosts.
The Trojan horse's signature has been added to the Dr.Web virus databases. Doctor Web recommends that all administrators of Linux servers perform a system check. If the file /lib/libkeyutils* (from 20 to 35 KB) is found in the system, it is a sign of infection.