November 1, 2012
Viruses
Various Trojan.Mayachok modifications lead among the threats detected by Dr.Web CureIt!, while BackDoor.IRC.NgrBot.42 files downloaded by the program are the most frequently found malignant files on disks. Java Runtime Environment Exploit.CVE2012-1723.13 ranks second, and Trojan.Mayachok.17994 is in third place, yet the absolute leader of the summer’s rankings, Trojan.Mayachok.1, has shifted to fourth position. Also detected in relatively large numbers were Trojan.SMSSend, Win32.HLLP.Neshta (a file infector in existence since 2005), Trojan.Mayachok.17986, the polymorphic file infector Win32.Sector.22, BackDoor.IRC.NgrBot.146, and BackDoor.Butirat.201. The top ten programs most frequently detected by Dr.Web CureIt! are listed in the table below.
| Threat | % |
|---|---|
| Trojan.MayachokMEM.4 | 2,34 |
| BackDoor.IRC.NgrBot.42 | 2,18 |
| Exploit.CVE2012-1723.13 | 1,64 |
| Trojan.Mayachok.17994 | 1,47 |
| Trojan.Mayachok.1 | 1,29 |
| Java.Downloader.697 | 1,18 |
| Trojan.SMSSend.2363 | 0,96 |
| Win32.HLLP.Neshta | 0,93 |
| Trojan.Mayachok.17986 | 0,82 |
| Win32.Sector.22 | 0,71 |
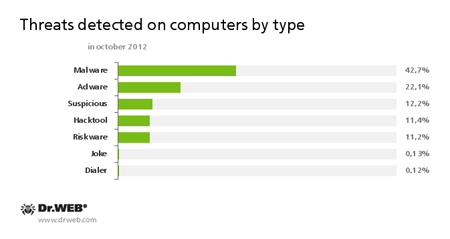
October threats are shown by class in the following diagram:
Botnets
Doctor Web continues to monitor changes in the number of bots in the most active botnets. The notorious Backdoor.Flashback.39 botnet, comprised of infected computers running Mac OS X, shrank very little to 105,730 hosts on October 30, compared with 109,372 bots known to be operational on September 30. While the Backdoor.Flashback.39 botnet ceased to grow, owners of Apple-compatible computers are apparently in no hurry to check their computers with an anti-virus to finally get rid of the Trojan.
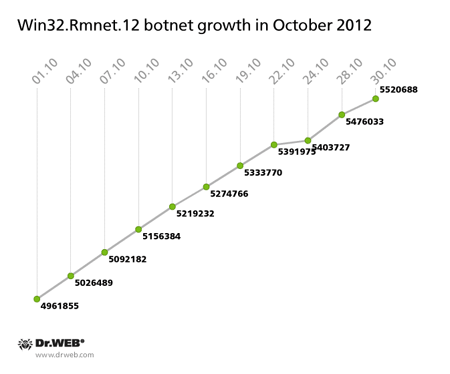
As expected, in early October the Win32.Rmnet.12 botnet exceeded the five million mark, and by the end of the month, it reached five and a half million infected hosts, thus beating its own September growth-rate record. The botnet’s growth is illustrated on the graph below:
It's already been mentioned that the file infector Win32.Rmnet.12 is mostly spreading on machines in Southeast Asia, but an infected 132,445 machines, which constitute 2.39% of the botnet’s size, reside in Russia.
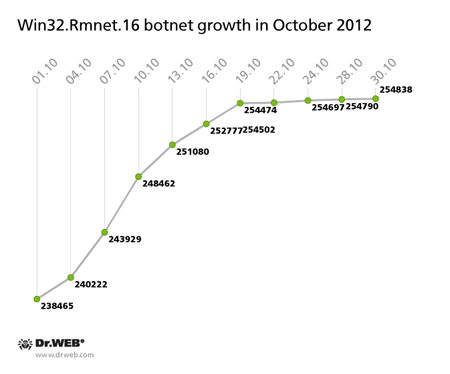
The Win32.Rmnet.12 botnet also continues to grow slowly—its progression is illustrated in the diagram below. On October 30, 2012, its total number of bots reached 254,838, which is 16,373 bots more than at the beginning of the month.
Malicious spam
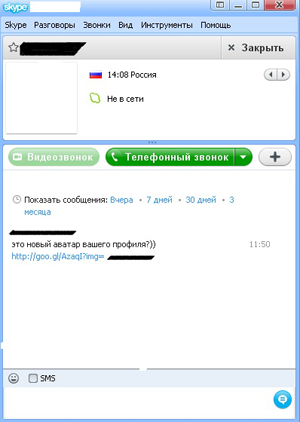
Early October was marked by a mass distribution via Skype of messages containing the link to a malignant file, created with the Google URL shortener. Users who clicked on the link were prompted to download a zip archive containing BackDoor.IRC.NgrBot.146. The malicious program that sent such messages via Skype was added to the Dr.Web database as Trojan.Spamlink.1.
Attackers who employ e-mail in their malicious schemes were more active in the second half of October. They spoofed Amazon.com, Microsoft, Fedex, PayPal, and several airline companies supposedly requiring booking confirmation. In most cases, such messages contained a link to a web page that redirected the user to another web site. Then, a JavaScript file loaded from the site is used to download two malicious programs: BackDoor.Andromeda.22 and Trojan.Necurs.97. We talked about similar malicious mailings in one of our news stories but still recommend that users exercise caution and do not click on links in e-mails from unknown senders.
Threats to Android
In terms of threats to Android, October 2012 was relatively calm. Several entries for Android.SmsSend programs were added to the Dr.Web virus databases during the month. Note that these Trojans send highly chargeable SMS messages and subscribe device owners to various services whose fees are credited from their account.
An entry for Trojan Android.FakeLookout.1.origin, which is spread via Google Play as a software update, was also added to the virus databases. This malware gained access to SMS messages and various files stored on a memory card and sent the data to a remote server. Despite the potential risk for personal information, the Trojan is not a serious threat to Android users, because at the time of its removal from Google Play, the number of its installations had not exceeded 50.
A new modification in the malware family Android.Gongfu was discovered in October. It was added to the virus database as Android.Gongfu.10.origin.
The threat of the month: Trojan.GBPBoot.1
Trojan.GBPBoot.1 turned out to be one of the most unusual malware found in October by Doctor Web's virus analysts.
As far as its malicious payload is considered, Trojan.GBPBoot.1 doesn't stand out among malicious programs. It downloads and launches various executable files in an infected system. Otherwise, the Trojan has no other harmful capabilities. However, this Trojan is unusual primarily because it strongly resists attempts to remove it.
When the Trojan infects a system, its first module modifies the master boot record on the hard disk and then writes—at the end of an appropriate partition (outside the file system)—the malicious installer code, its automatic restore module, an archive containing the explorer.exe file, and configuration data. The Trojan main file is implemented as a library registered on an infected computer as a system service.
If for any reason the malicious service file is deleted (for example, by anti-virus software), the self-restore routine springs into action. The malicious MBR code written by the Trojan checks whether the malignant service file is present on the hard drive. Both NTFS and FAT32 are supported. If the file is not found, Trojan.GBPBoot.1 replaces the file explorer.exe with its file that incorporates the self-restoring mechanism. The file is run at Windows’ startup. When launched, the malicious explorer.exe again initiates an infection, and then restores and launches the original explorer.exe. Thus, a simple scan of the system by various anti-virus programs may not lead to the expected result, since the Trojan is able to repair itself in the protected system.
Dr.Web software can detect and eliminate the threat, and also restores the compromised boot record. More details about Trojan.GBPBoot.1 can be found in a review published by Doctor Web.
Other threats in October
In early October, Doctor Web's analysts registered the spread of Trojan.Proxy.23012 which is designed to send spam. Detailed information about this threat can be found in a review published on news.drweb.com.
Another review was devoted to a Trojan-Downloader that spread intensively in October via the peer-to-peer network created with Trojan.PWS.Panda.2395. This malicious program employs a peculiar infection mechanism, described in detail at www.drweb.com.
Malicious files detected in mail traffic in Oktober
| 01.10.2012 00:00 - 31.10.2012 23:00 | ||
| 1 | Trojan.Necurs.97 | 1.40% |
| 2 | Trojan.Oficla.zip | 1.20% |
| 3 | JS.Redirector.145 | 1.13% |
| 4 | Trojan.PWS.Stealer.946 | 0.84% |
| 5 | JS.Redirector.150 | 0.80% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.58% |
| 7 | Exploit.CVE2010-3333.6 | 0.53% |
| 8 | BackDoor.Andromeda.22 | 0.53% |
| 9 | Trojan.PWS.Panda.786 | 0.47% |
| 10 | Trojan.DownLoader6.56603 | 0.47% |
| 11 | Win32.HLLM.MyDoom.33808 | 0.42% |
| 12 | Trojan.Siggen4.25819 | 0.42% |
| 13 | BackDoor.Kuluoz.3 | 0.38% |
| 14 | Trojan.Packed.18626 | 0.36% |
| 15 | Trojan.DownLoader7.6770 | 0.31% |
| 16 | Win32.HLLM.Beagle | 0.31% |
| 17 | Win32.HLLM.Netsky.35328 | 0.29% |
| 18 | Trojan.PWS.UFR.2334 | 0.29% |
| 19 | Trojan.Winlock.6566 | 0.27% |
| 20 | SCRIPT.Virus | 0.24% |
Malicious files detected on user computers in Oktober
| 01.10.2012 00:00 - 31.10.2012 23:00 | ||
| 1 | Adware.Downware.533 | 0.82% |
| 2 | SCRIPT.Virus | 0.51% |
| 3 | Tool.Unwanted.JS.SMSFraud.10 | 0.38% |
| 4 | Adware.Downware.179 | 0.34% |
| 5 | Tool.Skymonk.6 | 0.31% |
| 6 | Trojan.Fraudster.329 | 0.31% |
| 7 | Trojan.Fraudster.296 | 0.30% |
| 8 | Adware.Downware.426 | 0.29% |
| 9 | Win32.HLLW.Autoruner.59834 | 0.27% |
| 10 | Win32.HLLW.Shadow | 0.27% |
| 11 | Tool.Unwanted.JS.SMSFraud.15 | 0.26% |
| 12 | Trojan.Fraudster.320 | 0.26% |
| 13 | Trojan.Fraudster.344 | 0.25% |
| 14 | Trojan.Fraudster.347 | 0.25% |
| 15 | Adware.InstallCore.53 | 0.25% |
| 16 | Trojan.Siggen4.23472 | 0.24% |
| 17 | JS.IFrame.317 | 0.23% |
| 18 | Exploit.CVE2012-1723.13 | 0.23% |
| 19 | Trojan.SMSSend.2363 | 0.23% |
| 20 | Adware.Downware.316 | 0.23% |

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments