October 12, 2012
Infiltration of a targeted system is carried out with the help of the widespread Trojan.PWS.Panda.2395. First an encrypted executable file that contains the malicious module is downloaded via the peer-to-peer network. After a successful decryption, it launches another module that loads into the memory the image of another malicious application detected by Dr. Web as a Trojan.DownLoader program.
This program is saved into the user's folder as an executable with a random name and modifies the Windows Registry to enable its automatic launch at startup.
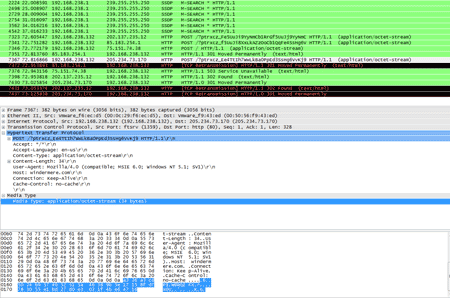
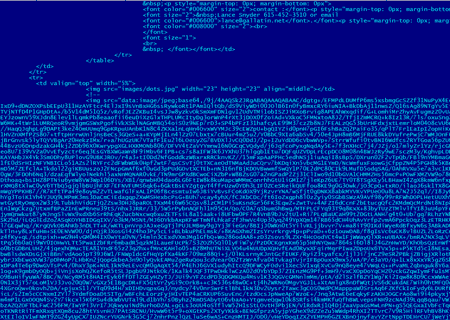
The Trojan utilizes an unusual procedure to download other malicious software onto the infected computer. The Trojan.DownLoader incorporates an encrypted list of domain names to which the program sends requests over HTTPS. In response, the Trojan obtains the main web page and parses the HTML code in the search for the image tag <img src="data:image/jpeg;base64 … >. The tag's attribute is encrypted malicious code which is extracted from the html document and decrypted. After that, depending on the instructions received, the code is either injected into the svchost.exe process launched by the Trojan or saved in a temporary folder. In addition, the DDoS module and the list of targets are extracted from the downloader component, and the malware's image is configured directly in its process.
Once loaded successfully, the DDoS module generates up to eight independent threads in which it continuously sends POST requests to the servers on the list and attempts to establish an SMTP connection with a number of hosts to which it sends random data. The list contains 200 selected target sites for a DDoS-attack. These include AOL-owned love.com, the sites of several major American universities, as well as msn.com, netscape.com and others.
But that’s not all. The Trojan uses a special routine to pick one domain name from the list, sends a request to the server, and gets a web page in return. In the page’s contents, the Trojan also attempts to find the insert image tag <img src="data:image ...> whose attribute contains the base-64 encrypted data array.
When decrypted, the data is saved to a file disguised as a JPEG image. This file also stores a container whose content is compressed with the gzip archiver. Finally, BackDoor.Bulknet.739, which is capable of sending spam, is extracted from the archive.
Signatures of all the malware have been added to Dr.Web's virus databases, so they pose no threat to systems protected by anti-viruses from Doctor Web.


![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments