February 1, 2012
Virus threats in January
The file infector Win32.Expiro.23 (19.23% of all detections) was the leader among malicious programs found on users' computers by Dr.Web CureIt! in January When launched, it attempts to elevate its privileges in the system, searches for running services and infects the corresponding executables.
Win32.Rmnet.8 (8.86% of infections) was not far behind. This virus gets onto computers from infected flash drives or when an infected executable file is run, and it can replicate itself. The program infects .exe, .dll, .scr, .html, .htm and, in some cases, .doc and .xls files, and can create autorun.inf files on removable storage devices. Immediately after its launch, Win32.Rmnet modifies the master boot record, registers Microsoft Windows Service (it can work as a rootkit in the system), attempts to remove RapportMgmtService and adds several malicious modules into the system that appear in the Windows Task Manager as four entries named iexplore.exe. Win32.Rmnet steals passwords from popular ftp-clients, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, Bullet Proof FTP. This information can later be exploited to carry out network attacks or to place various malicious objects on remote servers. Trojan.WMALoader and Trojan.Inor are also often found on infected computers of Russian users.
Financial affairs
A Trojan.PWS.Ibank sample fell into Doctor Web virus analysts' hands in early January. It is equipped to keep up with the latest online banking trends. This malicious program allows attackers to get user authentication data, keys and information about the configuration of many different banking applications. The distinguishing feature of this Trojan horse modification is its VNC-server functions. The server code provides support for the protocol used to communicate with a Zeus dedicated-server (Trojan.PWS.Panda) which, in fact, is used to control the malware remotely. This Trojan horse contains another important feature: a module that is designed to monitor and intercept information processed by specialized software used in one of Russia’s state-owned financial institutions.. Its architecture is rather complex. It can send intercepted information to criminals as well as execute various commands from a remote server in the infected system— including commands that may render the system non-operational. A detailed technical description of this program was promptly handed to law enforcement agencies by Doctor Web.
Around the same time, another malware was discovered—hackers intended to use this one for a phishing attack on Russian bank customers. Once the program has gotten into a system, Trojan.Hosts.5590 creates a new explorer.exe process containing its code and then places its file as Eldesoft.exe into the autorun folder.
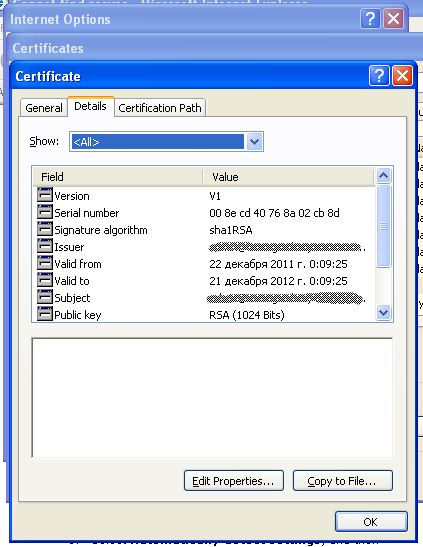
If the user accesses the bank's site via Microsoft Internet Explorer, the Trojan horse utilizes crypt32.dll to install a fake certificate. When a certificate is added to the store, the operating system usually shows a warning. The Trojan horse intercepts and closes the warning window.
If the bank site is accessed with a different browser, the standard library nss3.dll is used to install the certificate. Trojan.Hosts.5590 connects to a remote server and retrieves a configuration file that contains the IP address of the phishing server and domain names to be replaced. Later, whenever the user attempts to connect to the banking system via HTTPS, they will be displayed a fake web-page, and the account information they submit will be sent to criminals. Prompt and competent measures taken by the bank’s security service and efforts made by Doctor Web's specialists have ensured that the Trojan horse no longer poses a serious threat to users.
Windows lockers in decline
January 2012 saw a 25% decline in the number of support requests from users whose systems were affected by Windows blockers.
This welcome trend emerged due not only to the decrease in extortion malware but also to the recently launched https://www.drweb.com/xperf/unlockerportal that enables users to search for codes to unlock computers infected by Trojan.Winlock. Currently 13-15 thousand users visit the portal daily.
However, there are examples of extortionist programs that have no unlock code at all. These include, in particular, Trojan.Winlock.5490 which targets French users. Trojan.Winlock.5490, written in C, will only run in a system with French set as the default language. The Trojan horse incorporates anti-debugging features: when loaded, it checks whether its process has been launched in a VirtualBox, QEmu or VMWare environment. If so, the Trojan horse process is ended.
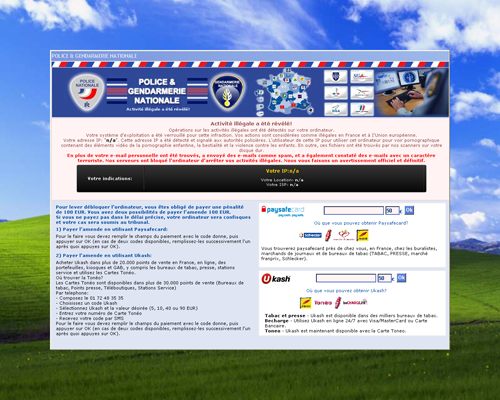
Once Trojan.Winlock.5490 is in the system, it starts an svchost.exe process with its injected code, orders Windows to hide the Task bar and stops all explorer.exe and taskmgr.exe process threads. Then the Trojan horse adds its registry entry to be launched automatically and displays a window containing a demand to pay 100 euros with a Paysafecard or Ukash card. The message language is French. Then the card number entered by the victim is sent to the remote command server and the user is informed that the payment will be processed in 24 hours.
Search results bring up malicious links
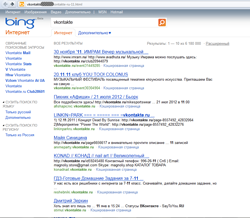
Techniques employed by criminals to spread links to malicious files and fraudulent sites are perfected on a monthly basis. These include all sorts of text disguise tricks and social engineering methods. In January, network con artists turned their attention to search engine result pages.
 |
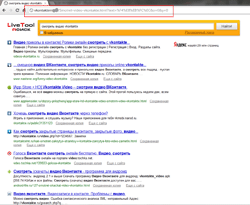 |
While searching the web, people often send several search requests in different tabs or browser windows. It is these pages that criminals fake, hoping that in the confusion a user won't notice an extra search result page. People also tend to trust search results more than ordinary link lists. In some cases, fraudsters even set up fake search engines, as did the founders of the search service LiveTool, whose interface is almost identical to the Yandex design, and the About Us link leads to a fraudulent site that mimics a VK page.
A fake search engine page may open automatically when clicking on a link found on a genuine search results page. In addition, a malicious SERP typically contains links relevant to the search initiated by the user and at first glance does not cause any suspicion. In turn, following links from this page may lead to a fraudulent site or resource, spreading malicious software. Currently, such links point to sites faking social networking resources or sites offering questionable services on a subscription basis as well as sites spreading Trojan.SmsSend malware.
In the recent past, criminals created a large number of fake social networking sites, but fake SERP or search engines are surely a new phenomenon.
Top 20 malware detected in January in mail traffic
| 01.01.2012 00:00 - 31.01.2012 18:00 | ||
| 1 | Trojan.DownLoad2.24758 | 974126 (28.66%) |
| 2 | Trojan.Oficla.zip | 831616 (24.47%) |
| 3 | Trojan.Tenagour.9 | 423106 (12.45%) |
| 4 | Trojan.Inject.57506 | 258383 (7.60%) |
| 5 | EICAR Test File (NOT a Virus!) | 198666 (5.84%) |
| 6 | Trojan.DownLoad2.32643 | 132938 (3.91%) |
| 7 | Trojan.Tenagour.3 | 110835 (3.26%) |
| 8 | Trojan.Siggen2.58686 | 66624 (1.96%) |
| 9 | Trojan.Siggen2.62026 | 66398 (1.95%) |
| 10 | Win32.HLLM.Netsky.18516 | 53409 (1.57%) |
| 11 | Trojan.DownLoad2.34604 | 44053 (1.30%) |
| 12 | Trojan.Packed.19696 | 44038 (1.30%) |
| 13 | Trojan.DownLoader5.26458 | 25809 (0.76%) |
| 14 | Trojan.Siggen.65070 | 24806 (0.73%) |
| 15 | Trojan.DownLoader4.5890 | 22291 (0.66%) |
| 16 | Trojan.DownLoader4.31404 | 22145 (0.65%) |
| 17 | Trojan.DownLoader5.886 | 21686 (0.64%) |
| 18 | Trojan.DownLoader4.61182 | 21133 (0.62%) |
| 19 | Trojan.PWS.Panda.1513 | 20104 (0.59%) |
| 20 | BackDoor.Bifrost.23284 | 6113 (0.18%) |
Total scanned: 1,149,052,932
Infected: 3,399,130 (0.30%)
Top 20 malware detected in January on user PCs
| 01.01.2012 00:00 - 31.01.2012 18:00 | ||
| 1 | Win32.Rmnet.12 | 23948173 (30.31%) |
| 2 | JS.Click.218 | 14651677 (18.54%) |
| 3 | JS.IFrame.117 | 8323572 (10.53%) |
| 4 | Win32.HLLP.Neshta | 8098226 (10.25%) |
| 5 | JS.IFrame.112 | 3734140 (4.73%) |
| 6 | JS.IFrame.95 | 3312785 (4.19%) |
| 7 | Trojan.IFrameClick.3 | 2716412 (3.44%) |
| 8 | Win32.Virut | 2672403 (3.38%) |
| 9 | Trojan.MulDrop1.48542 | 1946447 (2.46%) |
| 10 | Trojan.Hosts.5006 | 1369212 (1.73%) |
| 11 | Trojan.DownLoader.17772 | 906094 (1.15%) |
| 12 | Trojan.PWS.Ibank.474 | 562056 (0.71%) |
| 13 | Win32.HLLP.Whboy.45 | 415298 (0.53%) |
| 14 | Trojan.DownLoader5.18057 | 339809 (0.43%) |
| 15 | JS.IFrame.176 | 319449 (0.40%) |
| 16 | Trojan.Packed.22271 | 318517 (0.40%) |
| 17 | Trojan.PWS.Ibank.456 | 280158 (0.35%) |
| 18 | Trojan.DownLoader.42350 | 221567 (0.28%) |
| 19 | Win32.Virut.56 | 218322 (0.28%) |
| 20 | JS.Autoruner | 213647 (0.27%) |
Total scanned: 114,007,715,914
Infected: 79,017,655 (0.07%)

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments