The Cybercriminal World and Russia. 2011 Virus Activity Overview
Virus reviews | All the news | Virus alerts
January 11, 2012
In 2011 the number of threats for Android grew by 20 times
2011 saw a twenty-fold increase in the number of threats for Android, the vast majority of such malware belonging to the Android.SmsSend family. These applications are typically installers that allegedly contain the program one needs; however, to install it, one or more paid SMS messages must be sent. The essence of the fraud is that the user can download the application free of charge from its developer's website rather than pay criminals to download it.
In early 2011, the Dr.Web virus database contained only six entries for the Android.SmsSend Trojan family, while by December, the number of these threats had increased nearly 45-fold. The dynamics of the growth in the number of Android.SmsSend entries added to Dr.Web databases are shown in the chart below.
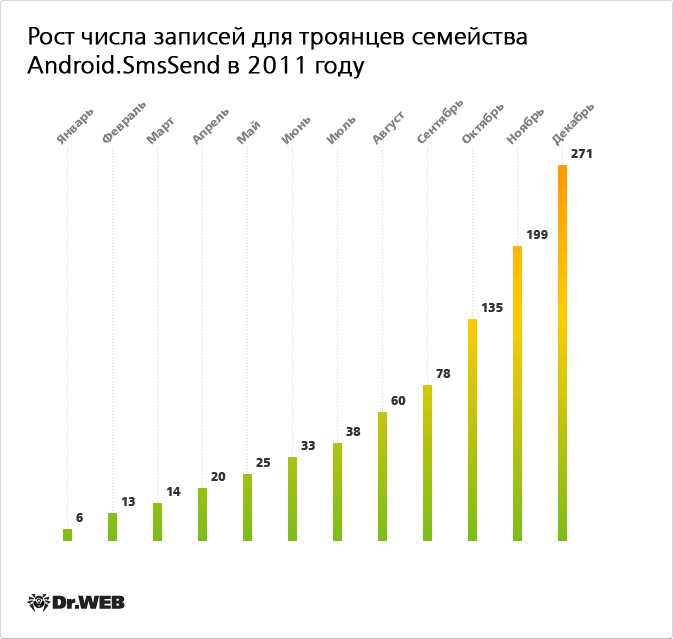
Considerable success in combating this type of threat is partly due to the use of the unique Origins Tracing™ technology developed by Doctor Web. Conventional detection technology requires a unique signature for each malicious file in order for an anti-virus to recognize such a file. With the use of the Origins Tracing technology in Dr.Web products, a special entry that describes the behaviour algorithm of the sample is generated for each malicious program, and is then added to a virus database. Just a single entry is enough to cover an entire family of malicious applications, which ensures prompt detection of new variants within a family and significantly reduces the size of virus databases.
As of the end of 2011, Dr.Web virus databases contained a total of 630 entries corresponding to malicious programs for Android, while at the beginning of the year there were only 30 of them. Thus, we can say that over the past 12 months, the total number of threats to the Android mobile platform has increased 20-fold. The diagram below shows the percentage distribution of various types of threats for Android.
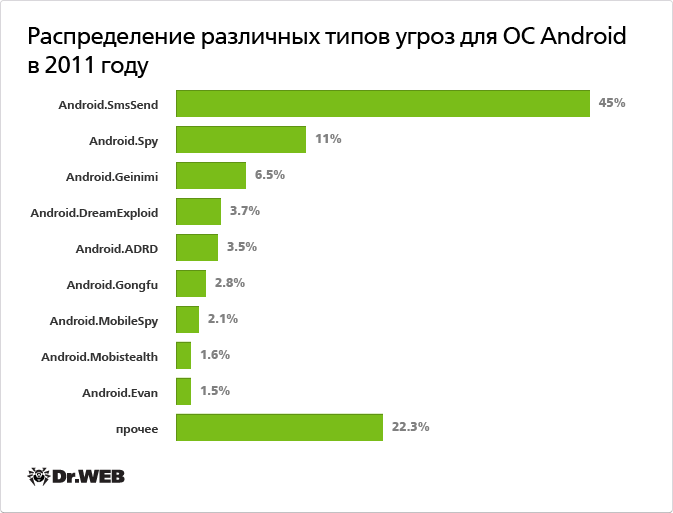
As a comparison, it should be noted that today there are 212 malware programs known for Symbian OS, and 30 for Windows Mobile, while the number of Trojans that can run on any mobile platform that supports Java is 923. Based on the above figures, we can conclude that, for 2011 alone, Android greatly exceeded its nearest competitors with regards to the number of specific threats to its operating system.
Rootkits
Rootkits are known to be malicious programs that can hide the traces of their presence in an operating system. As compared to the previous year, this type of threat is still spreading at the same speed. With 64-bit operating systems getting increasingly popular, virus writers are forced to adapt their creations, and, therefore, the number of rootkit variants running in user mode has increased severalfold. The most popular threats of this type are still BackDoor.Tdss and BackDoor.Maxplus.
In 2011, Doctor Web experts discovered a unique rootkit called Trojan.Bioskit.1that can infect a PC's BIOS—and only if Award Software’s BIOS is installed on a PC. Later on, attempts to spread another modified Trojan.Bioskit were detected, but due to errors in the code, this version of the Trojan does not represent any serious threat to users.
File viruses
File viruses are traditionally classified as malicious programs that infect, among other things, executables and can replicate themselves (i.e., capable of reproducing without user intervention). Based on the number of infections by year’s end, Win32.Rmnet.12 is the leader among file viruses. This virus was detected on users' computers 165,286,935 times, which equals 11.22% of all malware infections. Second place was taken by Win32.HLLP.Neshta, which was discovered 94,777,924 times throughout the year (6.44% of infections), and Win32.HLLP.Whboy.45 closed in on the top three (52,610,974 cases, which is 3.57% of the total).
In 2011, the family of file viruses was expanded with new malware instances: the leader on the list Win32.Rmnet.12, and Win32.HLLP.Novosel, and Win32.Sector.22, as well as many others.
Winlockers
Ransomware programs that prevent an operating system from being booted have long been well known, and over the past twelve months, the number of Trojan.Winlock family threat variants grew fairly as expected. The case was not without its surprises: in 2011, winlockers reached not only Russia’s neighbouring countries (where ransomware modifications specifically targeting users of Kazakhstan, Ukraine and Belarus were detected) but also European countries. In particular, discovered in September 2011, the Trojan.Winlock.3260 contains a multilingualtext of system locking messages taking the form of a notice from the local police department of the country in which the victim resides: for Germany, it is Bundespolizei; for the UK—the Metropolitan Police; and for Spain—La Policìa Española. In all cases, a victim is solicited to pay—via whatever payment system is widely used in their specific country— to have their system unlocked. Shortly thereafter, the number of such Trojans showed skyrocketing growth. This is most likely due to the fact that the Internet is getting increasingly more populated by affiliate programs organized by the creators of such ransomware: at specialist forums, attackers are actively looking for professionals to disseminate malicious software.
Since the beginning of the year, experts witnessed a more than twofold increase in the number of new Trojan.Winlock modifications. At the same time, the share of those who called Doctor Web technical support because of winlocker infections was 29.37% of the total number of calls.
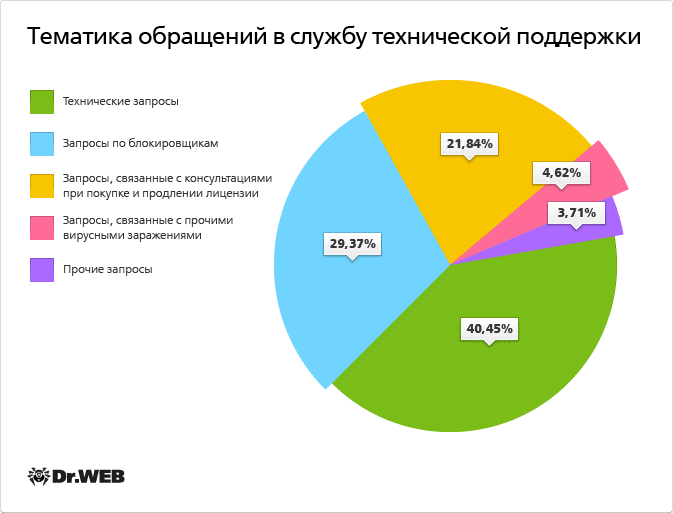
MBR lockers
The number of ransomware programs that infect the Master Boot Record (MBR) of PCs has also markedly increased. The first samples of extortion programs infecting the MBR of the hard drive came to the anti-virus lab in November 2010, and today they number over 300. Since 2011, the number of programs in the Trojan.MBRlock malware family has grown 52-fold, increasing from 6 to 316 identified modifications. There has also been a clear trend towards a change in the functionality of such Trojans—they are getting increasingly sophisticated and malicious: the first Trojan.MBRlock modification eventually disarmed itself automatically but not the latest versions; they are not only free of such a mechanism—they don’t even store an unencrypted unlock code, which renders them somewhat difficult to cure. For instance, Trojan.MBRlock.17, introduced in November 2011, differs from its predecessors in the fact that it writes its components into random sectors on the hard disk, while the unlock key is created dynamically based on a number of parameters. Today, it is one of the most dangerous MBR locker Trojan modifications.
Encoders
When getting on a PC, encoders, or, as they are sometimes called, encryptors, encrypt files stored on the hard disk by using a special algorithm, and require that the user pay a certain amount of money for the opportunity to gain access to that information. Around September 2011, a real outbreak of the Trojan.Encoder and Trojan.FolderLock malware family took place, having affected a great number of users. The range of versions of such threats also expanded: from the beginning of 2011, the number of entries in the databases for various types of encoders increased by 60%.
Online fraud
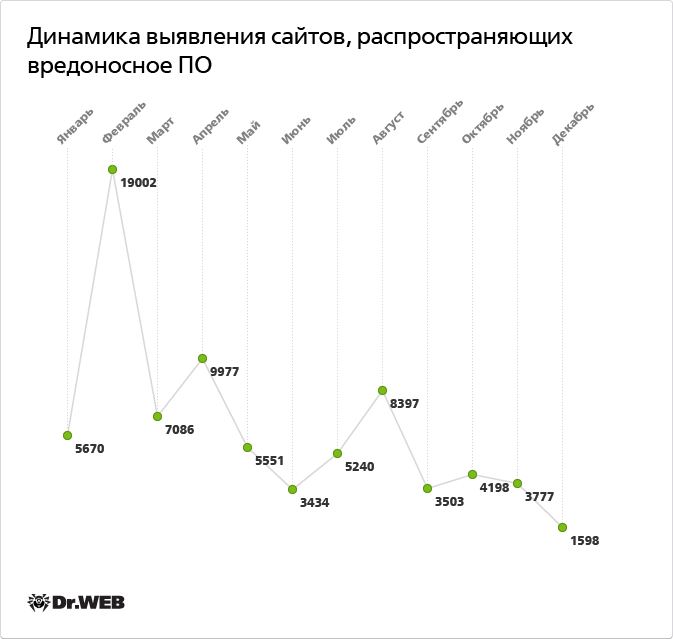
The number of fraud cases against Internet users is not decreasing: hackers keep using any methods available to force a user to send a paid SMS message or sign up for services that require a monthly subscription fee. The imaginations of online scammers are truly inexhaustible: everything is used, including fake prize draws and fake file-sharing networks. Crooks offer gullible users access to telephone and genealogical databases, ways to search for twins and relatives, have palms, stars, and Tarot cards read, and get individualized horoscopes and diets plans. More details on current online fraud schemes can be found in one of our information reviews. The dynamics of identifying fraudulent websites that use social engineering techniques can be traced on the chart below.
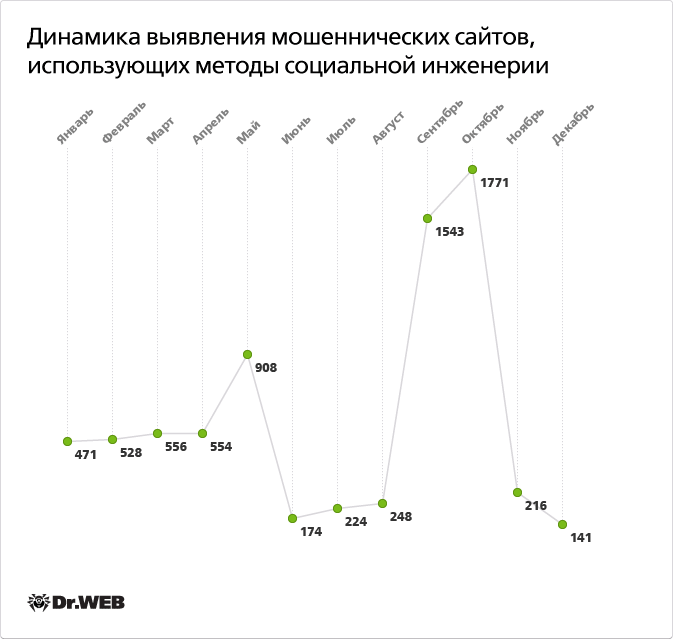
The sharp rise in the number of fraudster-owned online resources added to the databases in September and October was largely driven by "the September raids on underground websites", on which Doctor Web reported in one of its news releases. The event allowed a significant number of such resources to be unveiled—and the results of work done by the company's experts can be clearly seen in the diagram.
And here are the statistics for URLs from which malicious software was distributed in 2011, and which have been added to the databases:
Here we can see a reverse trend: the largest number of malicious resources was registered in the first half of the year, while there was a definite lull on this front with the onset of autumn.
The "hunt" for social network users also continues. In 2011, crooks were actively inventing new scams, the most popular of which we recently covered in a review article. In 2011, a lot of fake websites that mimic interfaces of popular social networks were revealed, and the addresses of such resources were added to the Dr.Web databases.
Banking Trojans
In the past year, Doctor Web virus analysts discovered a lot of malware designed to steal user information, including information for accessing online Bank-Client systems and e-wallets.
With its rich functionality, of particular concern is the family of Trojan.Winspy, new modifications of which appeared in the first half of 2011. Another malicious application of this kind has been added to the virus databases under the name of Trojan.Carberp.1. Like some other Trojan horse programs, Trojan.Carberp.1 has built-in protection from being analyzed with a debugger. Data hashing and injecting its code into several system processes are the key features of this Trojan horse. Trojan.Carberp.1 sends intruders banking service access information, steals keys and passwords from various programs, works as a key logger, takes screenshots, etc. In addition, the Trojan horse has a built-in module that allows it to receive and follow instructions from a remote command center. With this Trojan.Carberp.1 feature, attackers can visit websites anonymously by turning the victim's computer into a proxy server, download and run different files and send screen shots to a remote host, and even destroy the operating system.
Also quite common are Trojan.PWS.Ibank family viruses designed to steal online banking access data and able to unite compromised machines into botnets. Of course, we cannot ignore such a famous Trojan horse as Trojan.PWS.Panda, also known under the names of Zeus and Zbot. Its primary feature is to steal user passwords, although this Trojan has a wealth of capabilities. Zeus was very widespread and has posed a serious threat to banking system users for a long time. Another Trojan horse created for similar purposes is Trojan.PWS.SpySweep, also known under the name SpyEye. In addition, the first banking Trojan for the Android platform, Android.SpyEye.1, appeared in this year. If a user's computer is compromised by SpyEye, the risk of infection by Android.SpyEye.1 is significantly increased for the user's mobile device. When a user visits a bank site, whose address is present in the Trojan horse's configuration file, the malicious program injects contents such as text and web forms into the web page. Thus, when an unsuspecting victim loads into the browser of their desktop or laptop PC a web page of the bank where they have an account, they will see a message saying that the bank has implemented new security measures, and that the user must adhere to those new measures in order to gain access to the Bank-Client system. It is also suggested to them that they download a special application containing a Trojan to their mobile phone.
After the victim downloads and installs Android.SpyEye.1 on their mobile device, it starts to intercept and send all incoming SMS messages to the intruders. Android.SpyEye.1 may present danger to owners of mobile devices since it is capable of transferring confidential information into the hands of intruders.
The most interesting threats of 2011
In February and March 2011, intruders carried out a malicious attack on the terminals of one of the most common payment systems in Russia, using the program Trojan.PWS.OSMP. This malicious program interferes with the work of the legal process maratl.exe running in the terminal operating system, and substitutes the account number into which a user pays. Thus, the money went directly to the attackers.
Trojan.PWS.OSMP is one of the first malware programs to pose a risk to payment terminal customers. In essence, the Trojan allows attackers to modify any number of the account to which a customer is transferring money. Another modification of this malware stole a configuration file from the terminal that supposedly can help attackers create a fake terminal on a regular computer and forward money to their own account electronically, bypassing the cash acceptor.
One more Trojan program worth mentioning is BackDoor.Dande. This Trojan steals information from client applications used to order pharmaceutical products. Data collected include information on the software installed on a computer, user account passwords, etc. We can assume that attackers are primarily interested in data on prices and quantities of medication orders. All the stolen information is encrypted and transmitted to a server controlled by criminals. To put it another way, this is a rare instance of a Trojan horse being designed to steal information related to a particular type of business.
During the year, some very interesting malicious programs also appeared for the Android mobile platform. Among them is the Android.Gone.1, a Trojan that only needs 60 seconds to steal all the information stored in an Android mobile phone, including contacts, messages, recent calls, browser history, etc. Stolen data are downloaded into a website specially created by virus writers. One must pay five dollars to gain access to the stolen information. Another interesting "Threat of the Year" for this mobile platform was the Android.DreamExploid Trojan that, unbeknownst to users, tried to obtain greater privileges with the smartphone’s software. That is, instead of the standard restricted access, the user gained the permissions of a system administrator. Also, Android.DreamExploid can download programs from the Internet and install them, and is capable of gathering information on the infected device and sending it to attackers.
2012 Expected Trends
In 2012, further growth in the number of threats to the Android mobile operating system should be expected. In addition, blocker programs for this platform are very likely to emerge. This forecast is primarily stipulated by the fact that mobile operating systems make it much easier for intruders to access a victim's wallet. To profit from a desktop OS user is not that easy—for example, you need to lock Windows first, and then force the user to reach a pay terminal or type and send SMS. To the contrary, an infected mobile phone can send short messages to paid numbers, display advertising, and download paid ringtones and other content, gradually writing off money from the operator account. This black market is huge, and is now actively being developed by hackers, and modern mobile platforms with their extensive functionality open wonderful opportunities for this.
One can expect the spread of highly specialized threats targeted at industrial automation systems. This includes automated process control systems, access control, monitoring, heating, air-conditioning and ventilation, and other computerized systems for industrial and manufacturing organizations. Supervisory control and data acquisition (SCADA) infrastructure may be jeopardized. Doctor Web analysts note that malware exploiting the vulnerability of such systems can be especially dangerous since such complexes are used in key industries such as electricity, transportation, mining, oil and gas.
It is highly likely that new, technically improved threats targeting banking systems and banking access data will emerge. Perhaps, attackers won't limit themselves to user PCs and Bank-Client systems and will attack banking structures or even state-owned financial institutions. There will appear new, previously unknown methods of fraud, both with regards to phishing websites and to social networks. The dynamics of new fraud schemes show that attackers use virtually all technologies available to them, and with the advent of new features on social networking sites, fraudsters will probably incorporate those new features to achieve their nefarious goals. For example, in 2011, cybercriminals employed file-sharing features embedded in social networks, videos, and even add-ons to Mozilla Firefox browser to trick users taking part in voting activities. It is thought that their arsenal is not going to be limited to that in the future, and cybercriminals will continue to seek new methods of raking in illicit earnings.
Top 20 malware detected in 2011 in mail traffic
| 01.01.2011 00:00 - 31.12.2011 12:00 | ||
| 1 | Trojan.Oficla.zip | 6227166 (18.64%) |
| 2 | Win32.HLLM.MyDoom.33808 | 3319848 (9.94%) |
| 3 | Win32.HLLM.Netsky.18401 | 2760140 (8.26%) |
| 4 | Trojan.DownLoad2.24758 | 2288568 (6.85%) |
| 5 | Trojan.DownLoad1.58681 | 1590498 (4.76%) |
| 6 | Trojan.Packed.20878 | 1146053 (3.43%) |
| 7 | Win32.HLLW.Texmer.51 | 1118340 (3.35%) |
| 8 | Trojan.MulDrop.64589 | 1028999 (3.08%) |
| 9 | Win32.HLLM.Netsky.35328 | 1015202 (3.04%) |
| 10 | BackDoor.Pushnik.15 | 891865 (2.67%) |
| 11 | Trojan.Packed.20312 | 701617 (2.10%) |
| 12 | Trojan.DownLoad.41551 | 656401 (1.96%) |
| 13 | Trojan.Inject.57506 | 497520 (1.49%) |
| 14 | Trojan.Tenagour.9 | 413183 (1.24%) |
| 15 | Win32.HLLM.Beagle | 407862 (1.22%) |
| 16 | Trojan.Oficla.38 | 397622 (1.19%) |
| 17 | Trojan.PWS.Siggen.12160 | 396715 (1.19%) |
| 18 | BackDoor.Pushnik.16 | 350835 (1.05%) |
| 19 | Trojan.MulDrop1.54160 | 346882 (1.04%) |
| 20 | Trojan.Tenagour.3 | 340629 (1.02%) |
Total scanned: 181,136,303,763
Infected: 33,407,612 (0.02%)
Top 20 malware detected in 2011 on user PCs
| 01.01.2011 00:00 - 31.12.2011 12:00 | ||
| 1 | JS.Click.218 | 649941902 (41.66%) |
| 2 | Win32.Rmnet.12 | 191646201 (12.28%) |
| 3 | Win32.HLLP.Neshta | 101340344 (6.50%) |
| 4 | JS.IFrame.95 | 97233222 (6.23%) |
| 5 | Trojan.IFrameClick.3 | 73541845 (4.71%) |
| 6 | Win32.Siggen.8 | 73120975 (4.69%) |
| 7 | Win32.HLLP.Whboy.45 | 52610974 (3.37%) |
| 8 | JS.IFrame.112 | 51610991 (3.31%) |
| 9 | Trojan.Mayachok.1 | 31307098 (2.01%) |
| 10 | Win32.HLLP.Novosel | 28110942 (1.80%) |
| 11 | Win32.Virut | 22052927 (1.41%) |
| 12 | JS.IFrame.117 | 19982870 (1.28%) |
| 13 | Trojan.MulDrop1.48542 | 12240506 (0.78%) |
| 14 | Win32.HLLP.Whboy.101 | 10055899 (0.64%) |
| 15 | Trojan.Click.64310 | 9525911 (0.61%) |
| 16 | JS.Click.222 | 9510719 (0.61%) |
| 17 | Win32.HLLP.Rox | 7974734 (0.51%) |
| 18 | Win32.HLLP.Whboy | 6537319 (0.42%) |
| 19 | Win32.HLLW.Whboy | 5690725 (0.36%) |
| 20 | HTTP.Content.Malformed | 5507122 (0.35%) |
Total scanned: 17,743,716,899,610,753
Infected: 1,560,049,362 (0.00%)