August 1, 2011
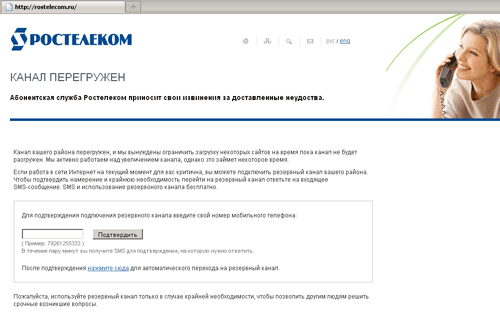
The last week-end saw a wave of infection when users suddenly were unable to surf the web and instead of the requested sites in the browser window they were displayed a message stating that the channel in their area was overloaded, so access to certain sites was restricted until more bandwidth would be available. Further, it offered users to take advantage of the back-up channel. To confirm the intention and the urgent need to switch to a backup channel, they had to reply to an incoming short message. If a user did submit their phone number through the web-form and replied to the message, a certain amount of money was withdrawn from their mobile account.
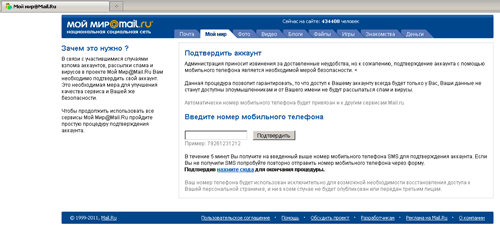
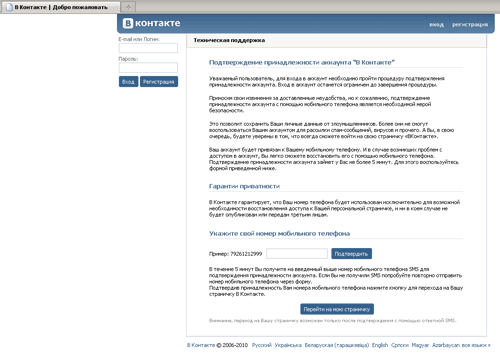
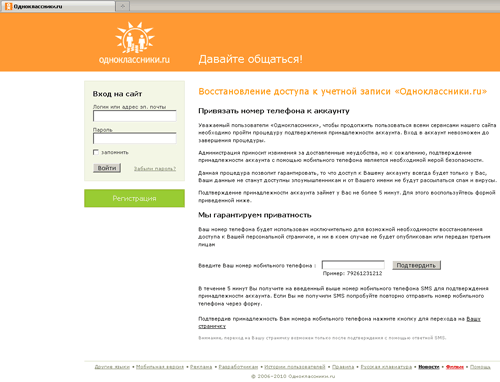
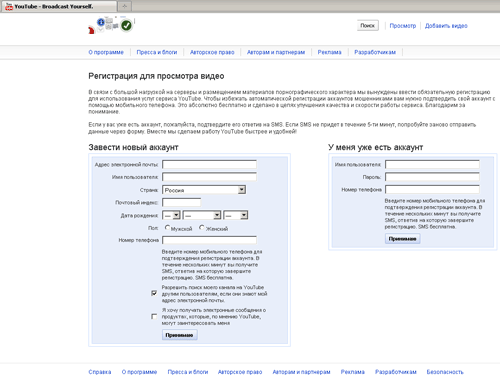
In other cases, when users tried to load web-pages of certain social networking and ISPs' sites in a browser window, the Trojan horse redirected them to a certain address, showing a web page that offered them to "activate" or "confirm" their account by specifying their phone number and replying to the incoming SMS.
When launched in an infected system, the Trojan horse creates a library with a name generated using the current hard drive partition serial number in the system32 directory, copies itself into a temporary folder as flash_player_update.exe and starts launching the file at 10 second intervals. Then the Trojan horse modifies the Windows registry and restarts the computer. After that Trojan.Mayachok.1 saves its configuration file to
C:\Documents and Settings\All Users\Application Data\cf. This file contains the list of blocked sites, control server addresses, and scripts embedded into web-pages requested by a user.
This Trojan horse is detected by scanning computer disks and doesn't pose a threat to Dr.Web anti-virus and Dr.Web Security Space users, as well as to those who use Dr.Web Enterprise Security Suite and to Dr.Web anti-virus service subscribers. If you have already become a victim of this Trojan horse, update the virus definitions and scan the disks on your computer. Besides, you can use the Dr.Web LiveCD emergency recovery or the Dr.Web CureIt! utility.
Doctor Web once again recommends that users be wary of links to various applications found in messages distributed among visitors of social networking sites.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments