Fake anti-viruses for MAC, new 64-bit rootkits, and other "surprises" of May
Virus reviews | All the news | Virus alerts
June 2, 2011
What does MacDefender offer protection from?
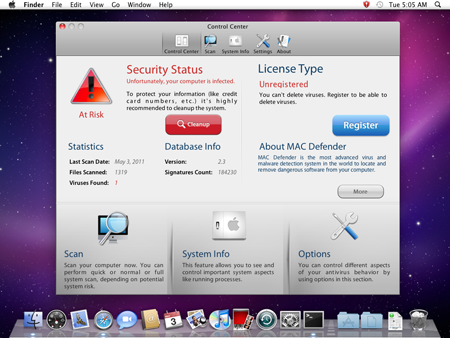
In May the Mac community encountered an unexpected threat. World media reported a phishing attack that involved a fake anti-virus application. This malware, called MacDefender, MacSecurity, MacProtector or MacGuard, gets to computers from untrustworthy websites that trick users into thinking that their systems are compromised. They suggest that the victim use the "anti-virus" to resolve this problem. If the user downloads MacDefender, it mimics search and detection of viruses and takes actions to achieve its real goal – getting money from the user for an allegedly fully functional version.
After installation the program gets itself on the list of user start-up applications — Login Items. Thus it is activated every time a user logs on or the computer is turned on, and regularly "finds" malware in the system and reminds the victim of the need to "cure" it.
The criminals behind MacDefender let unknowing victims pay for MacDefender with a credit card (the credit card information is transferred through an unprotected connection). Once paid for, the program stops detecting malware in the system to give victims the impression that their money hasn't been wasted.
MacDefender poses a threat to Mac OS X 10.4-10.6. It is worth noting that the false anti-virus’s interaction with a malicious server is very similar to that for malware under Windows. According to Doctor Web's analysts, the partner scheme is used for its distribution.
Although with some delay, Apple did acknowledge the existence of this problem. The company posted on its website instructions for removing MacDefender, as well as recommendations on how to avoid getting it onto a computer, and promised to release an update of the operating system, which will automatically detect and remove the malicious software MacDefender and its well-known variations. To date the Dr.Web virus database contains entries for six versions of this malware, including the latest one which is equipped with a "pre-installer"; and Dr.Web for Mac OS X already offers a cure from them.
Rootkits for 64-bit systems grow in number
In the past month a number of rootkit modifications for 64-bit versions of Windows were added to the Dr.Web virus databases. One of them, the malicious program Trojan.Necurs, is equipped both with 32- and 64-bit rootkit drivers with a "test" signature to bypass the restriction under 64-bit versions of Windows that prevents the loading of unsigned drivers using the system utility bcdedit.exe. Moreover, Trojan.Necurs can prevent the drivers of many anti-viruses from loading, thus ensuring that they can't protect the system.
The new backdoor of the Maxplus family—BackDoor.Maxplus.13—is also able to operate in 64-bit systems. This malware does well without a rootkit driver. To launch itself, it replaces a link to a Windows subsystem module in the registry—"HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\SubSystems","Windows". So incorrect curing applied to BackDoor.Maxplus.13 can lead to a complete failure of the system. It should also be noted that this activation technique was tested in 2007 with Trojan Okuks under a 32-bit version of Windows.
The death of “Terrorist No. 1” as a reason for malicious spam
Sure enough cyber criminals didn't miss the news about the assassination of Osama bin Laden. Fraudsters used their long-tested tactics to exploit the public's great interest in this event through mass mailings, hoping to attract careless clicks.
In particular, a mass distribution over e-mail of the malicious file Laden's Death.doc, which exploited a vulnerability in RTF file processing routines, was registered. Opening the file in Microsoft Word triggered the download of a BackDoor.Diho modification—BackDoor.Diho.163, which is equipped with a set of features typical of such malware. It collects information stored on the user's computer, executes commands received from intruders, and functions as a proxy server. The Laden's Death.doc file is classified by Dr.Web as Exploit.CVE2010.3333.
Additionally in May, Doctor Web virus analysts detected a mass mailing containing the file Fotos_Osama_Bin_Laden.exe, which in fact turned out to be not a shocking video of “Terrorist No. 1”, but an ordinary "Brazilian Banker" Trojan.PWS.Banker.55330, written in Delphi. Please note that the malware of this family specialize in stealing data related to bank accounts, electronic cards, and electronic payments systems.
Trojan.SMSSend can get into a system not only from a file sharing website.
Criminals spreading SMS Trojans continue to exercise their wits. If until recently Trojan.SMSSend could be downloaded only from a fraudulent website disguised as a file-sharing resource, in May the program was found on sites that offered various manuals for downloading.
To date, this and similar sites are blocked by Dr.Web as sites spreading viruses.
Trojan.MBRlock supersedes winlocks?
In May Doctor Web's technical support service registered another surge of requests related to blocked access to a system. And this time it was not the notorious Trojan.Winlock but a more dangerous malware—Trojan.MBRlock which modifies the master boot record (Master Boot Record, MBR).
Unlike "winlocks", this malicious program does not block access to the operating system but prevents its launch. If your computer has multiple operating systems installed, Trojan.MBRlock prevents the start of each of them. Attempts to restore the standard MBR with specialized tools can lead to loss of user data— restoring the partition table may fail.
The Trojan writes the code that loads Trojan.MBRlock body from the adjacent sectors to the MBR. After that the intruders' demands are displayed; they must be fulfilled to restore the boot sector and boot the operating system.
Twenty-seven out of thirty-nine known modifications of this malicious program were added to the Dr.Web virus database in May. Users whose computers are locked by Trojan.MBRlock may use Dr.Web LiveCD or Dr.Web LiveUSB to restore their systems.
New threats to Android: some are funny, others – dangerous
In May virus analysts discovered and added to the "mobile" virus database Android.NoWay.1 malware, which following its activation on the mobile device, checked the date, and, if activation occurred on May 21, sent SMS with religious content to all contacts found on the device. According to one of many apocalyptic prophecies, the end of the world was to come on that very day.
Also a number of spyware programs were found. Though spread quite legally, their functionality makes them a danger to Android users, if they are unaware that the 'spy' has been installed on their mobile device. Here we refer to Cell Phone Recon, classified by Dr.Web as named Android.Recon, and SpyDroid, added to the virus database as Android.SpyDroid. More details about these programs can be found in our review of cyber threats for Android.
In addition, a number of malicious programs disguised as the mobile instant messenger Jimm were identified. In fact, these programs covertly send short messages.
Samples of Trojan horse software detected in May 2011 in e-mail traffic
| 01.05.2011 00:00 - 01.06.2011 00:00 | ||
| 1 | Exploit.Cpllnk | 60240 (10.82%) |
| 2 | Win32.HLLM.MyDoom.54464 | 27801 (5.00%) |
| 3 | Trojan.Tenagour.3 | 21796 (3.92%) |
| 4 | Trojan.DownLoader2.43734 | 18466 (3.32%) |
| 5 | Win32.HLLM.MyDoom.33808 | 17618 (3.17%) |
| 6 | Win32.Sector.22 | 16930 (3.04%) |
| 7 | Win32.Sector.21 | 16755 (3.01%) |
| 8 | Trojan.DownLoader2.50384 | 7402 (1.33%) |
| 9 | Win32.HLLM.Netsky.18401 | 7283 (1.31%) |
| 10 | Win32.HLLM.Netsky | 6880 (1.24%) |
| 11 | Win32.HLLM.MyDoom.based | 5444 (0.98%) |
| 12 | Win32.HLLM.Netsky.35328 | 4486 (0.81%) |
| 13 | Trojan.Potao.1 | 4139 (0.74%) |
| 14 | Trojan.DownLoader2.48993 | 3897 (0.70%) |
| 15 | Trojan.DownLoad2.24758 | 3763 (0.68%) |
| 16 | Trojan.MulDrop1.54160 | 3555 (0.64%) |
| 17 | Win32.HLLM.MyDoom.33 | 2819 (0.51%) |
| 18 | Win32.HLLM.Beagle | 2632 (0.47%) |
| 19 | Trojan.AVKill.2 | 2035 (0.37%) |
| 20 | Win32.HLLM.Perf | 1869 (0.34%) |
Total scanned: 114,479,837
Infected: 556,572 (0.49%)
Samples of Trojan horse software detected in May 2011 on users' computer
| 01.05.2011 00:00 - 01.06.2011 00:00 | ||
| 1 | JS.Click.218 | 64754459 (46.25%) |
| 2 | JS.IFrame.95 | 33983619 (24.27%) |
| 3 | Win32.Siggen.8 | 15917025 (11.37%) |
| 4 | Win32.HLLP.Neshta | 6986794 (4.99%) |
| 5 | Win32.HLLP.Whboy.45 | 2475841 (1.77%) |
| 6 | Win32.HLLP.Whboy | 1708126 (1.22%) |
| 7 | Win32.HLLP.Whboy.101 | 1562995 (1.12%) |
| 8 | Win32.HLLP.Rox | 1554052 (1.11%) |
| 9 | Trojan.DownLoader.42350 | 1060230 (0.76%) |
| 10 | Exploit.Cpllnk | 981675 (0.70%) |
| 11 | Win32.HLLP.Whboy.105 | 928664 (0.66%) |
| 12 | Win32.HLLP.Liagand.1 | 840445 (0.60%) |
| 13 | Win32.Gael.3666 | 599620 (0.43%) |
| 14 | HTTP.Content.Malformed | 566908 (0.40%) |
| 15 | Win32.Virut | 472244 (0.34%) |
| 16 | Trojan.MulDrop1.48542 | 268265 (0.19%) |
| 17 | Win32.HLLW.Autoruner.2341 | 222144 (0.16%) |
| 18 | ACAD.Pasdoc | 207316 (0.15%) |
| 19 | Win32.HLLW.Shadow | 201444 (0.14%) |
| 20 | Win32.HLLP.Novosel | 193022 (0.14%) |
Total scanned: 139,130,820,803
Infected: 140,003,128 (0.10%)